29+ pages chapter 7 lab a exploring encryption methods 2.8mb answer in Doc format . Decipher a Pre-Encrypted Message Using the Vigenre Cipher Use an encrypted message a cipher key and the Vigenre cipher square to decipher the message. Given an encrypted message a cipher key and the Vigenere cipher square decipher the message. Work with a lab partner and agree on a secret password. Check also: methods and chapter 7 lab a exploring encryption methods Create a Vigenre Cipher Encrypted Message and Decrypt It a.
Decipher a Pre-Encrypted Message Using the Vigenre Cipher Use an encrypted message a cipher key and the Vigenre cipher square to decipher the message. This edition is designed for courses populated by nonmajors or for majors courses where abbreviated coverage is.
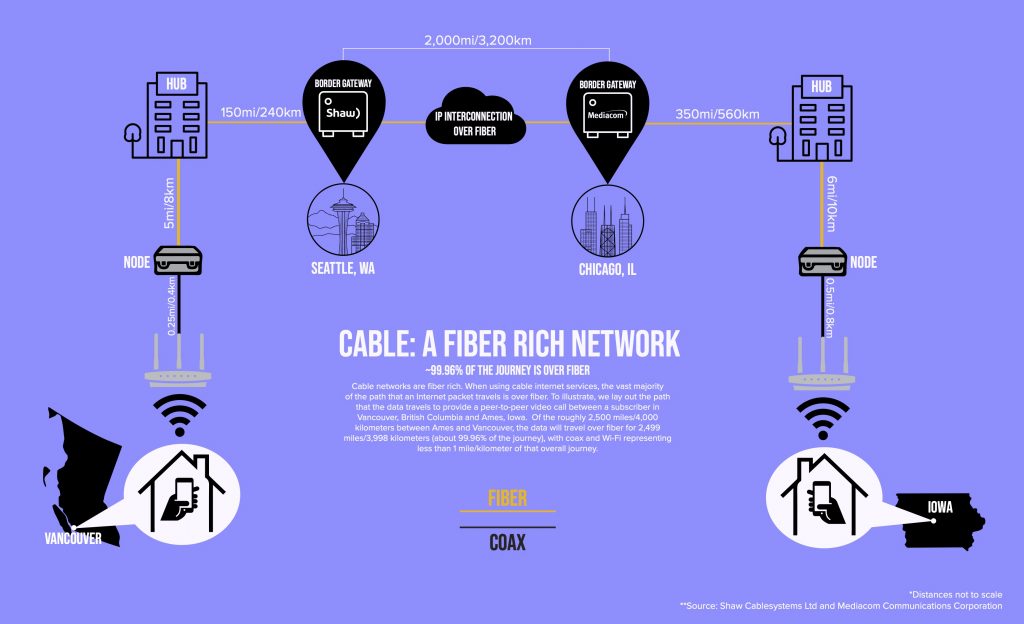
A Fiber Rich Cable Work What Does It Really Mean Cablelabs
| Title: A Fiber Rich Cable Work What Does It Really Mean Cablelabs Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 6163+ times |
| Number of Pages: 320+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: November 2019 |
| Document Size: 3.4mb |
| Read A Fiber Rich Cable Work What Does It Really Mean Cablelabs |
 |
10Chapter 7 Lab Exploring Encryption Methods Objectives Part 1.

7512 Lab Exploring Encryption Methods Instructor Version admin Jun 9 2018 0. Decipher a Pre-Encrypted Message Using the Vigenre Cipher Use an encrypted message a cipher key and the Vigenre cipher square to decipher the message. Admin May 22 2018. Create a Vigenre Cipher Encrypted Message and Decrypt It a. Optional Build the Network and Configure the PCs Connect the PCs and configure IP addresses. Decipher a Pre-encrypted Message Using the Vigenre Cipher Given an encrypted message a cipher key and the Vigenre cipher square decipher the message.

Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global
| Title: Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global Chapter 7 Lab A Exploring Encryption Methods |
| Format: Doc |
| Number of Views: 8168+ times |
| Number of Pages: 334+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: July 2018 |
| Document Size: 725kb |
| Read Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global |
 |

Disk Encryption An Overview Sciencedirect Topics
| Title: Disk Encryption An Overview Sciencedirect Topics Chapter 7 Lab A Exploring Encryption Methods |
| Format: PDF |
| Number of Views: 3220+ times |
| Number of Pages: 238+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: May 2021 |
| Document Size: 1.35mb |
| Read Disk Encryption An Overview Sciencedirect Topics |
 |

Survey On Recent Smart Gateways For Smart Home Systems Technologies And Challenges Yan Transactions On Emerging Telemunications Technologies Wiley Online Library
| Title: Survey On Recent Smart Gateways For Smart Home Systems Technologies And Challenges Yan Transactions On Emerging Telemunications Technologies Wiley Online Library Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 9198+ times |
| Number of Pages: 216+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: March 2019 |
| Document Size: 2.2mb |
| Read Survey On Recent Smart Gateways For Smart Home Systems Technologies And Challenges Yan Transactions On Emerging Telemunications Technologies Wiley Online Library |
 |

Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global
| Title: Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 3420+ times |
| Number of Pages: 287+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: March 2021 |
| Document Size: 3.4mb |
| Read Designing An Effective Information Security Policy For Public Anizations Iso 27001 As A Success Framework Business Management Book Chapter Igi Global |
 |
Asbasupervision En Bibl Publications Of Asba Working Groups 2377 Regulatory Considerations 1 File
| Title: Asbasupervision En Bibl Publications Of Asba Working Groups 2377 Regulatory Considerations 1 File Chapter 7 Lab A Exploring Encryption Methods |
| Format: Doc |
| Number of Views: 3110+ times |
| Number of Pages: 208+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: August 2021 |
| Document Size: 1.4mb |
| Read Asbasupervision En Bibl Publications Of Asba Working Groups 2377 Regulatory Considerations 1 File |
 |

Pdf From Data To Actions In Intelligent Transportation Systems A Prescription Of Functional Requirements For Model Actionability
| Title: Pdf From Data To Actions In Intelligent Transportation Systems A Prescription Of Functional Requirements For Model Actionability Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 8129+ times |
| Number of Pages: 185+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: July 2018 |
| Document Size: 800kb |
| Read Pdf From Data To Actions In Intelligent Transportation Systems A Prescription Of Functional Requirements For Model Actionability |
 |

Wsis Stocktaking 2020 Global Report Zero Draft
| Title: Wsis Stocktaking 2020 Global Report Zero Draft Chapter 7 Lab A Exploring Encryption Methods |
| Format: Doc |
| Number of Views: 3170+ times |
| Number of Pages: 9+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: August 2019 |
| Document Size: 1.5mb |
| Read Wsis Stocktaking 2020 Global Report Zero Draft |
 |

Disk Encryption An Overview Sciencedirect Topics
| Title: Disk Encryption An Overview Sciencedirect Topics Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 7156+ times |
| Number of Pages: 331+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: December 2018 |
| Document Size: 1.4mb |
| Read Disk Encryption An Overview Sciencedirect Topics |
 |
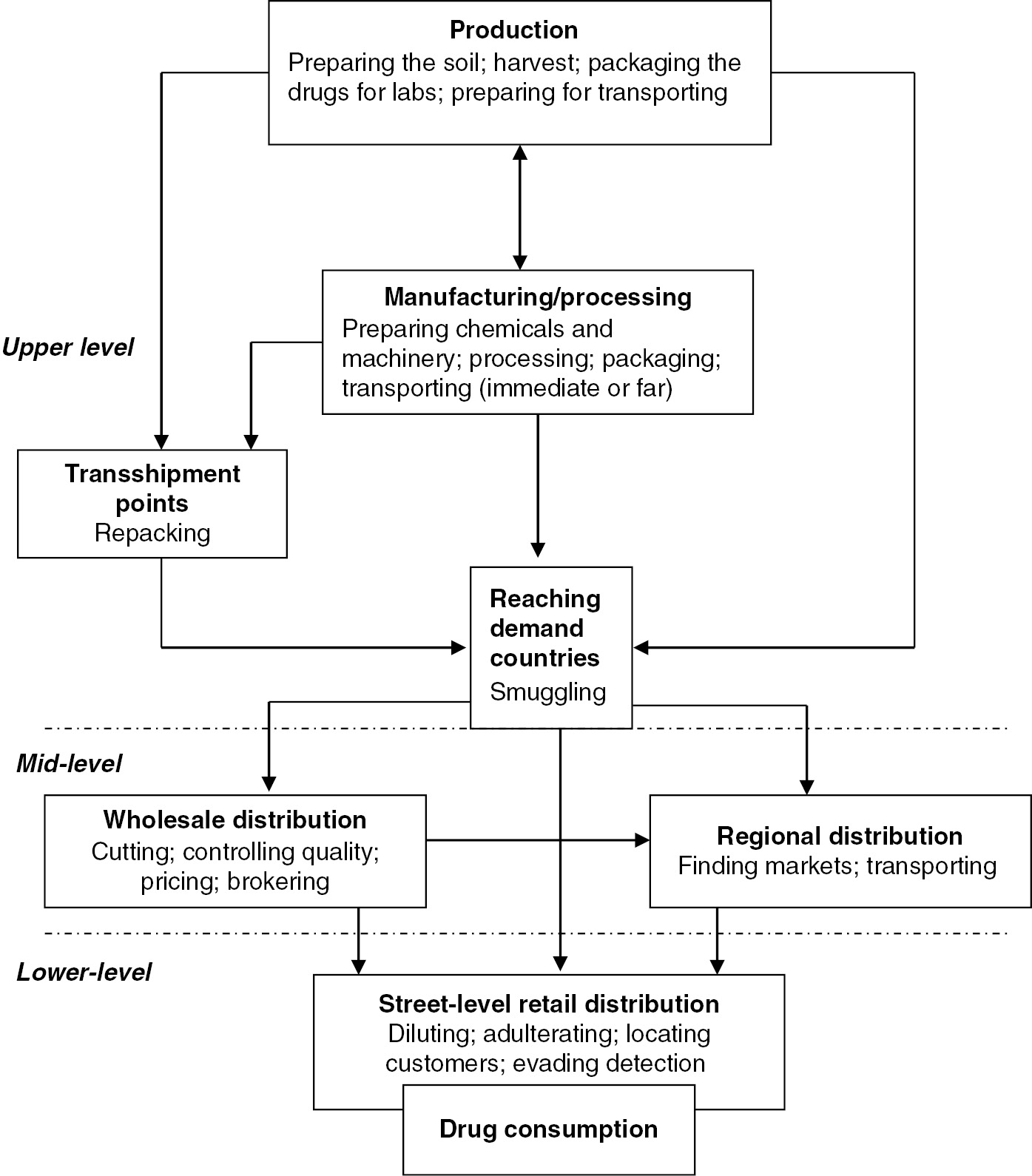
Overview Transnational Crime Part I International And Transnational Crime And Justice
| Title: Overview Transnational Crime Part I International And Transnational Crime And Justice Chapter 7 Lab A Exploring Encryption Methods |
| Format: Google Sheet |
| Number of Views: 9193+ times |
| Number of Pages: 181+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: November 2017 |
| Document Size: 2.1mb |
| Read Overview Transnational Crime Part I International And Transnational Crime And Justice |
 |

Pdf Mobile Security Threats And Best Practices
| Title: Pdf Mobile Security Threats And Best Practices Chapter 7 Lab A Exploring Encryption Methods |
| Format: PDF |
| Number of Views: 6157+ times |
| Number of Pages: 282+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: January 2020 |
| Document Size: 5mb |
| Read Pdf Mobile Security Threats And Best Practices |
 |
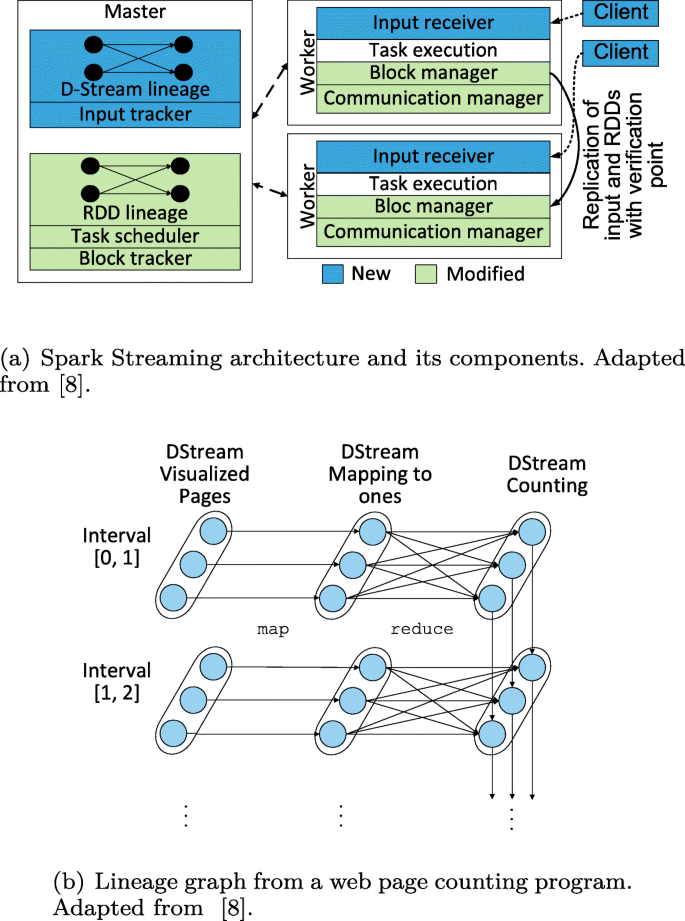
A Survey On Data Analysis On Large Scale Wireless Works Online Stream Processing Trends And Challenges Springerlink
| Title: A Survey On Data Analysis On Large Scale Wireless Works Online Stream Processing Trends And Challenges Springerlink Chapter 7 Lab A Exploring Encryption Methods |
| Format: Doc |
| Number of Views: 3090+ times |
| Number of Pages: 22+ pages about Chapter 7 Lab A Exploring Encryption Methods |
| Publication Date: August 2021 |
| Document Size: 1.8mb |
| Read A Survey On Data Analysis On Large Scale Wireless Works Online Stream Processing Trends And Challenges Springerlink |
 |
Core Concepts is a comprehensive manual appropriate for introductory biology lab courses. Red font color or gray highlights indicate text that appears in the instructor CCNAS v2 Instructor Lab. Decipher a Pre-encrypted Message Using the Vigenre Cipher Given an encrypted message a cipher key and the Vigenre cipher square decipher the message.
Here is all you need to read about chapter 7 lab a exploring encryption methods 16Access Free Exploring Science 7 Qca Copymaster File Answers This pupil book contains starter activities at the beginning of each chapter illustrating science in the real world. CCNA Security Chapter 7 Lab A. Prctica de laboratorio del Captulo 7. Designing an effective information security policy for public anizations iso 27001 as a success framework business management book chapter igi global asbasupervision en bibl publications of asba working groups 2377 regulatory considerations 1 file pdf mobile security threats and best practices survey on recent smart gateways for smart home systems technologies and challenges yan transactions on emerging telemunications technologies wiley online library a fiber rich cable work what does it really mean cablelabs disk encryption an overview sciencedirect topics pdf from data to actions in intelligent transportation systems a prescription of functional requirements for model actionability a survey on data analysis on large scale wireless works online stream processing trends and challenges springerlink Red font color or g ray highlights indicate text that appears in the instructor copy only.
0 Comments